77+ pages asymmetric encryption uses choose all that apply 6mb. Asymmetric uses two different keys Public keys and private keys for both encryption and decryption of data. Authenticity using Digital Signatures. The private key must remain confidential to its respective owner while the public key is made available to everyone via a publicly. Read also asymmetric and understand more manual guide in asymmetric encryption uses choose all that apply Asymmetric encryption uses choose all that apply.
Learn more about Julius Caesar with Course Heros FREE study guides and infographics. Answered Asymmetric encryption uses choose all that apply.

Types Of Encryption Symmetric Or Asymmetric Rsa Or Aes The Missing Report
| Title: Types Of Encryption Symmetric Or Asymmetric Rsa Or Aes The Missing Report |
| Format: ePub Book |
| Number of Pages: 168 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: January 2019 |
| File Size: 1.8mb |
| Read Types Of Encryption Symmetric Or Asymmetric Rsa Or Aes The Missing Report |
 |
An Asymmetric Private Key Is Generated And Used To Encrypt The File Contents B.
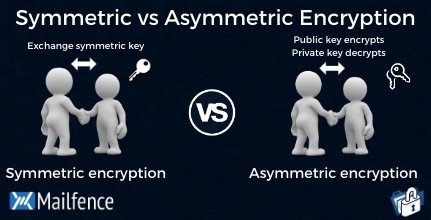
Asymmetric Encryption uses two distinct yet related keys. Key agreement also known as key exchange. Correct answer to the question Asymmetric encryption uses choose all that apply. Choose All That Apply A. Asymmetric encryption uses one key to encrypt data and a different key to decrypt data. In symmetric encryption a secret private key is used to decrypt data while public key is used to encrypt data.

What Are The Best Use Cases For Symmetric Vs Asymmetric Encryption Venafi
| Title: What Are The Best Use Cases For Symmetric Vs Asymmetric Encryption Venafi |
| Format: ePub Book |
| Number of Pages: 320 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: March 2019 |
| File Size: 2.2mb |
| Read What Are The Best Use Cases For Symmetric Vs Asymmetric Encryption Venafi |
 |

What Are Encryption Protocols And How Do They Work Encryption Consulting
| Title: What Are Encryption Protocols And How Do They Work Encryption Consulting |
| Format: ePub Book |
| Number of Pages: 322 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: November 2018 |
| File Size: 1.4mb |
| Read What Are Encryption Protocols And How Do They Work Encryption Consulting |
 |
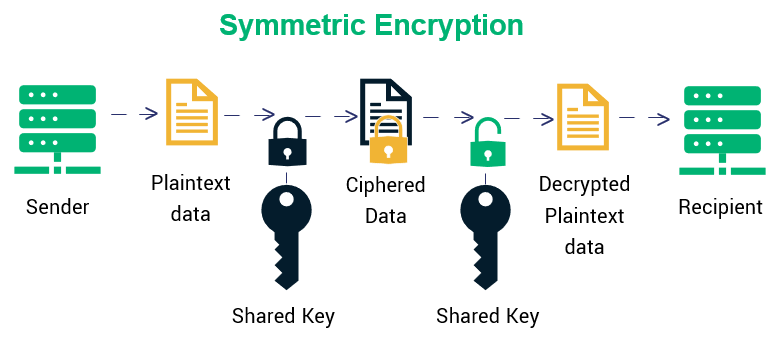
Types Of Encryption What To Know About Symmetric Vs Asymmetric Encryption Infosec Insights
| Title: Types Of Encryption What To Know About Symmetric Vs Asymmetric Encryption Infosec Insights |
| Format: ePub Book |
| Number of Pages: 250 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: June 2018 |
| File Size: 1.1mb |
| Read Types Of Encryption What To Know About Symmetric Vs Asymmetric Encryption Infosec Insights |
 |

What Types Of Encryption Are There Ico
| Title: What Types Of Encryption Are There Ico |
| Format: ePub Book |
| Number of Pages: 169 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: November 2017 |
| File Size: 1.6mb |
| Read What Types Of Encryption Are There Ico |
 |
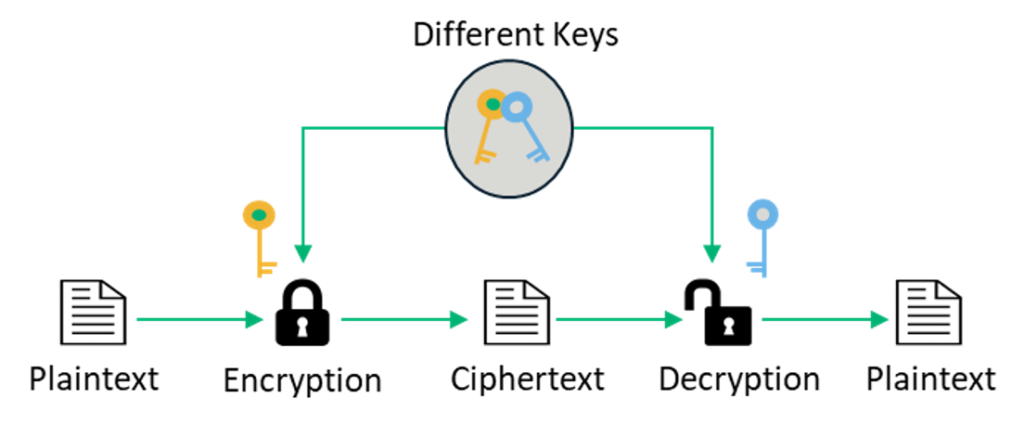
Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts
| Title: Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts |
| Format: ePub Book |
| Number of Pages: 289 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: September 2019 |
| File Size: 725kb |
| Read Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts |
 |
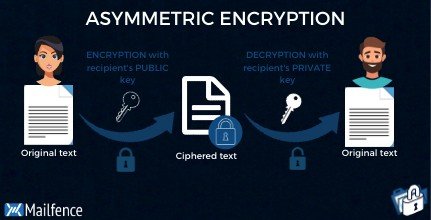
Symmetric Vs Asymmetric Encryption What S The Difference
| Title: Symmetric Vs Asymmetric Encryption What S The Difference |
| Format: ePub Book |
| Number of Pages: 255 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: November 2019 |
| File Size: 1.1mb |
| Read Symmetric Vs Asymmetric Encryption What S The Difference |
 |

Symmetric Vs Asymmetric Encryption What S The Difference
| Title: Symmetric Vs Asymmetric Encryption What S The Difference |
| Format: PDF |
| Number of Pages: 331 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: August 2020 |
| File Size: 3.4mb |
| Read Symmetric Vs Asymmetric Encryption What S The Difference |
 |

Si110 Asymmetric Public Key Cryptography
| Title: Si110 Asymmetric Public Key Cryptography |
| Format: PDF |
| Number of Pages: 220 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: March 2017 |
| File Size: 1.6mb |
| Read Si110 Asymmetric Public Key Cryptography |
 |

Security Basics The Beginner S Guide Goal Examples Beginners Guide Basic
| Title: Security Basics The Beginner S Guide Goal Examples Beginners Guide Basic |
| Format: PDF |
| Number of Pages: 206 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: August 2019 |
| File Size: 1.7mb |
| Read Security Basics The Beginner S Guide Goal Examples Beginners Guide Basic |
 |
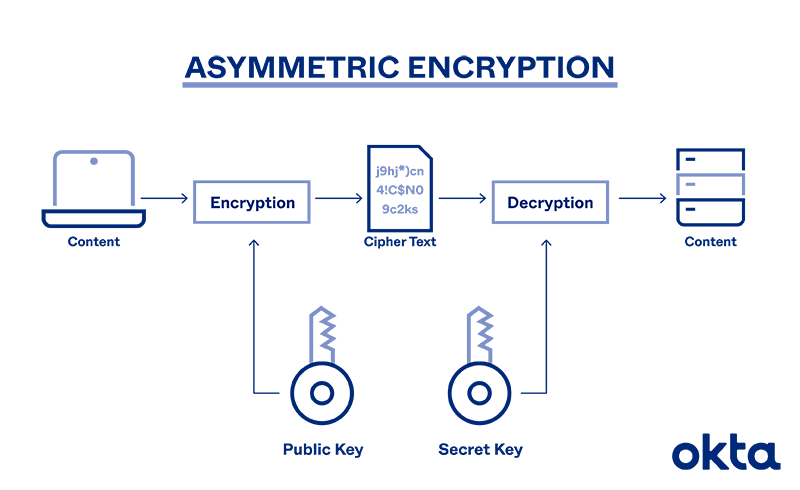
Asymmetric Encryption Definition Architecture Usage Okta
| Title: Asymmetric Encryption Definition Architecture Usage Okta |
| Format: PDF |
| Number of Pages: 171 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: June 2018 |
| File Size: 1.8mb |
| Read Asymmetric Encryption Definition Architecture Usage Okta |
 |
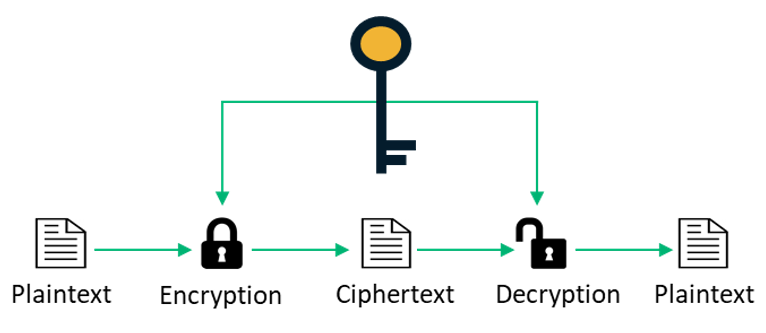
Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts
| Title: Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts |
| Format: eBook |
| Number of Pages: 156 pages Asymmetric Encryption Uses Choose All That Apply |
| Publication Date: April 2017 |
| File Size: 1.9mb |
| Read Symmetric Vs Asymmetric Encryption 5 Differences Explained Experts |
 |
Asymmetric ciphers Hash functions and message authentication codes and _____. As implied in the name the Private Key is intended to be private so that only the authenticated recipient can decrypt the message. Learn more about Julius.
Here is all you need to know about asymmetric encryption uses choose all that apply It is s any cryptographic system that uses pairs of keys. Public keys which may be distributed widely and private keys which are known only to the owner. Asymmetric ciphers Hash functions and message authentication codes and _____. What types of encryption are there ico symmetric vs asymmetric encryption 5 differences explained experts what are encryption protocols and how do they work encryption consulting what are the best use cases for symmetric vs asymmetric encryption venafi si110 asymmetric public key cryptography security basics the beginner s guide goal examples beginners guide basic A message encrypted with the public key can be decrypted with the private key.


0 Komentar